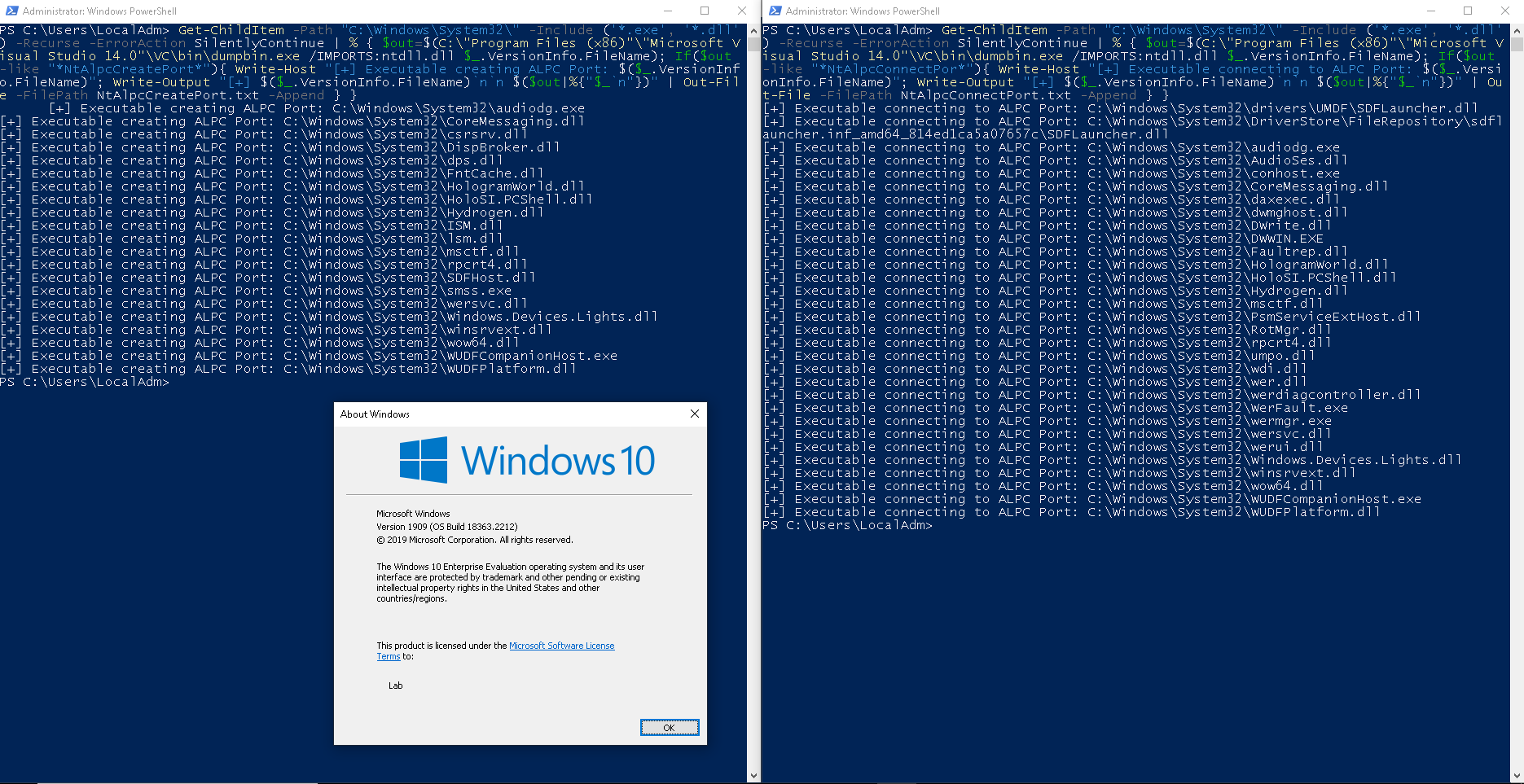
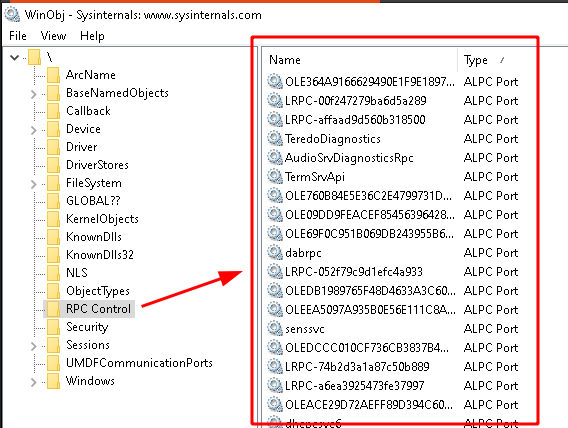
Jonas L on Twitter: "These files are hard links to the same file in system32- so if you setacl on the one in sxs it also applies to the one in system32" /

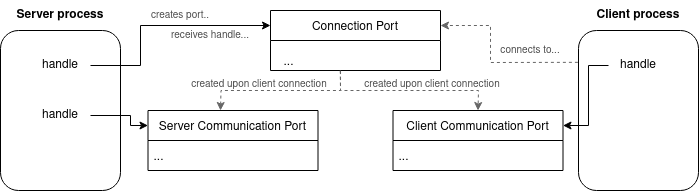
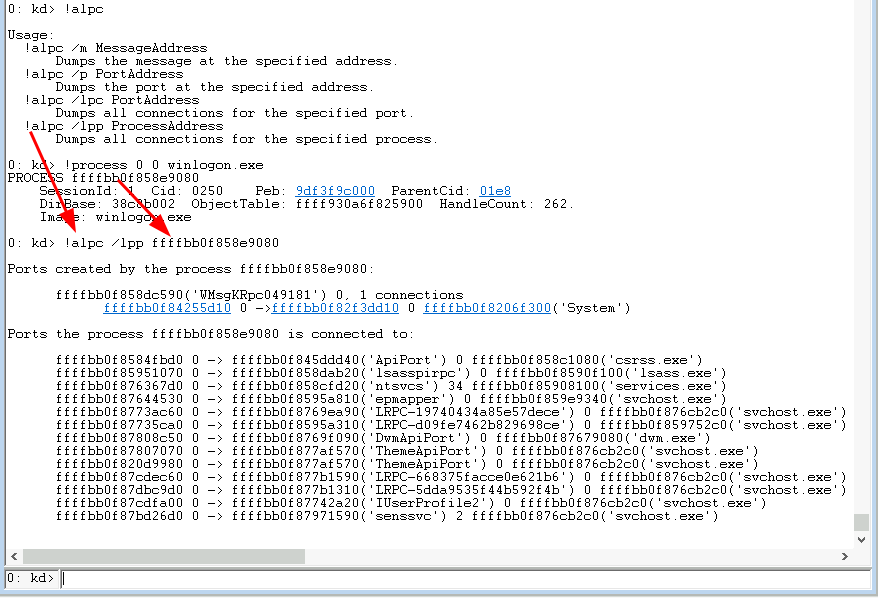
Yarden Shafir on Twitter: "In more @SystemInformer news, @jxy__s and @aionescu did amazing work mapping process connections over ALPC ports https://t.co/arLwsWmWIb" / Twitter



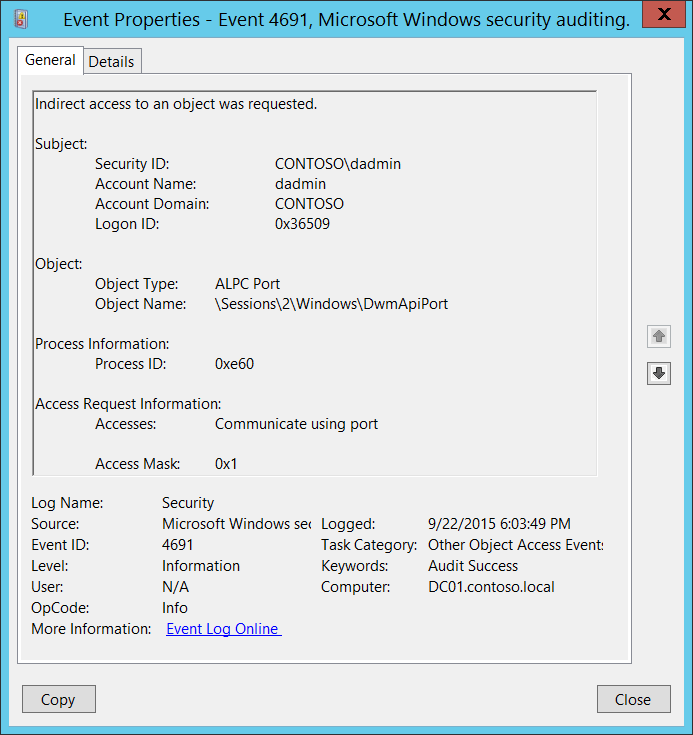
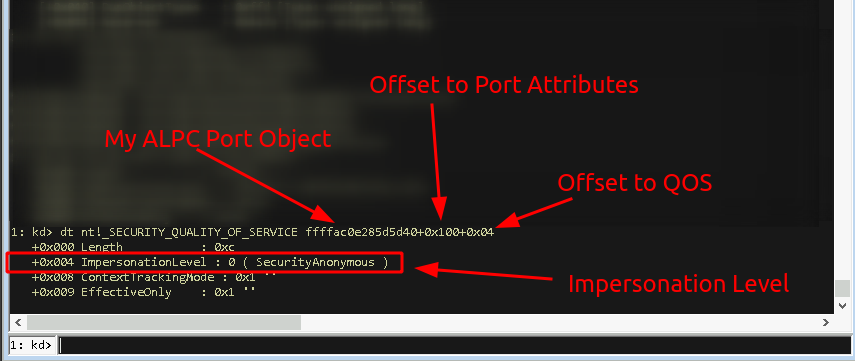
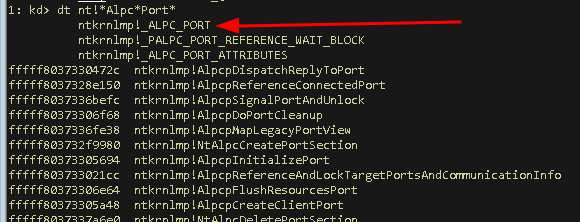
![New Attacks to Disable and Bypass Windows Management Instrumentation [LABSCon Edition] New Attacks to Disable and Bypass Windows Management Instrumentation [LABSCon Edition]](https://binarly.io/images/blog/New_Attacks_to_Disable_and_Bypass_Windows_Management_Instrumentation_LABSCon_Edition/Figure8.png)
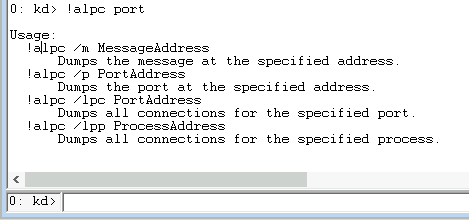
![New Attacks to Disable and Bypass Windows Management Instrumentation [LABSCon Edition] New Attacks to Disable and Bypass Windows Management Instrumentation [LABSCon Edition]](https://binarly.io/images/blog/New_Attacks_to_Disable_and_Bypass_Windows_Management_Instrumentation_LABSCon_Edition/Figure7.png)


![原创]win10 1909逆向(ALPC通信原理浅析)-软件逆向-看雪论坛-安全社区|安全招聘|bbs.pediy.com 原创]win10 1909逆向(ALPC通信原理浅析)-软件逆向-看雪论坛-安全社区|安全招聘|bbs.pediy.com](https://bbs.kanxue.com/upload/attach/202106/814951_8ETXHN6JTDRHBBC.jpg)