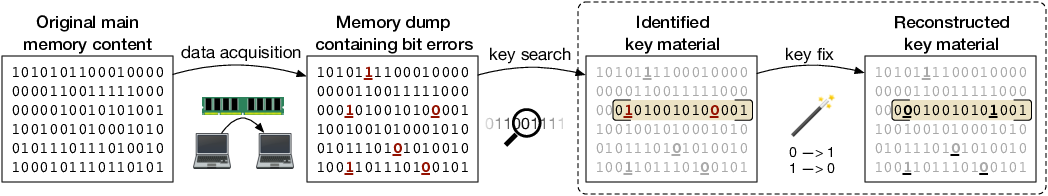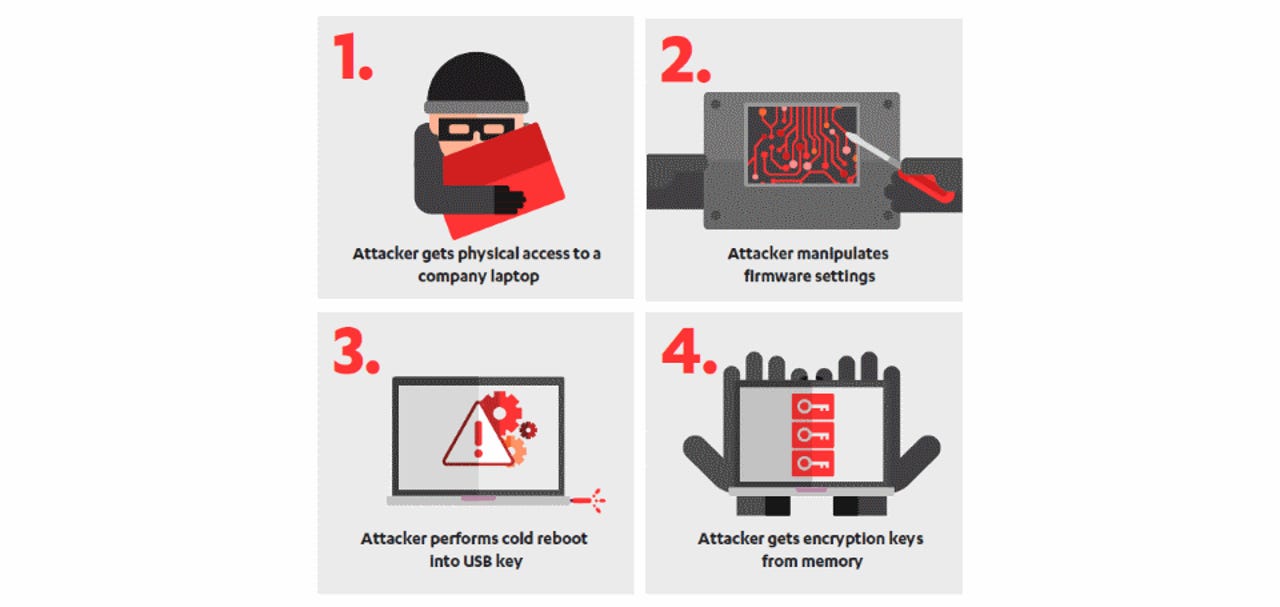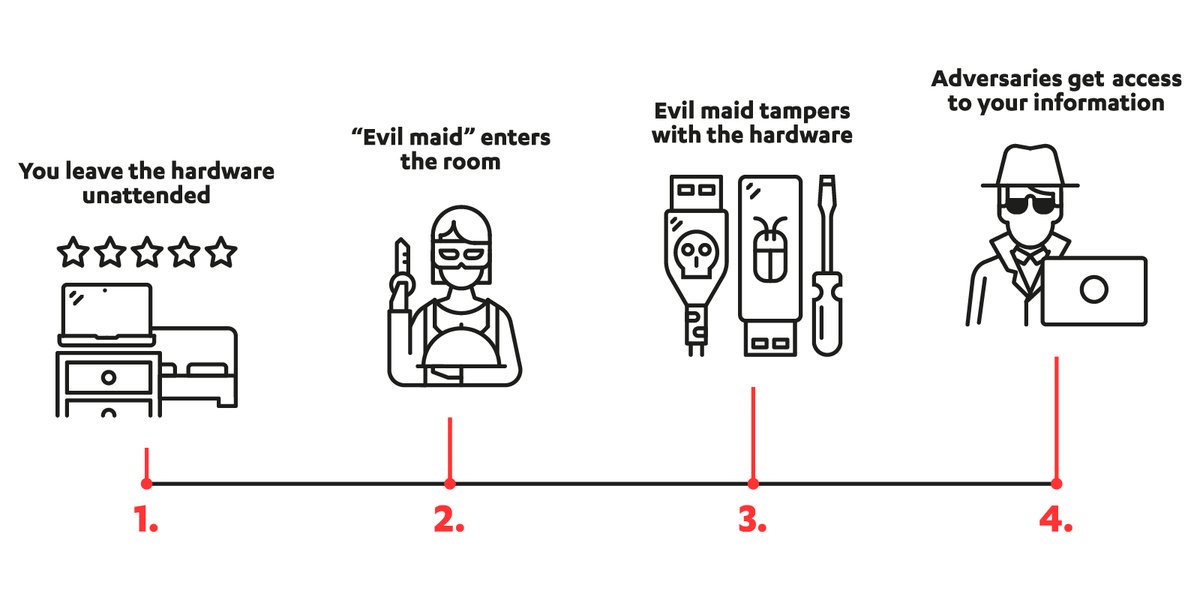
WithSecure™ on Twitter: "@nxsolle What's a cold boot attack? It starts with an attacker getting their hands on a laptop. https://t.co/r14cDD8M1O https://t.co/kgUht2491L" / Twitter

Almost All Computers Vulnerable to New Cold Boot Attack: F-Secure - Science news - Tasnim News Agency | Tasnim News Agency