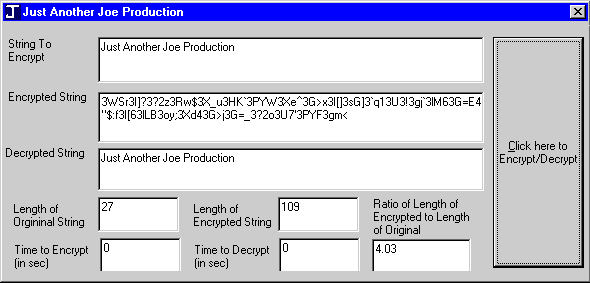
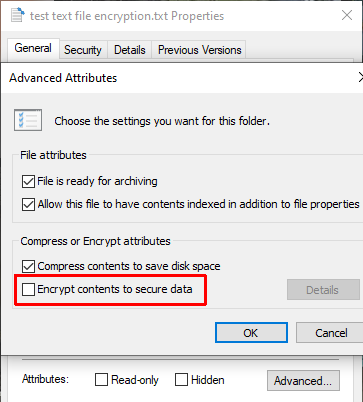
encryption - In .NET, can I encrypt a string using a private key, then decrypt it with a public key? - Stack Overflow
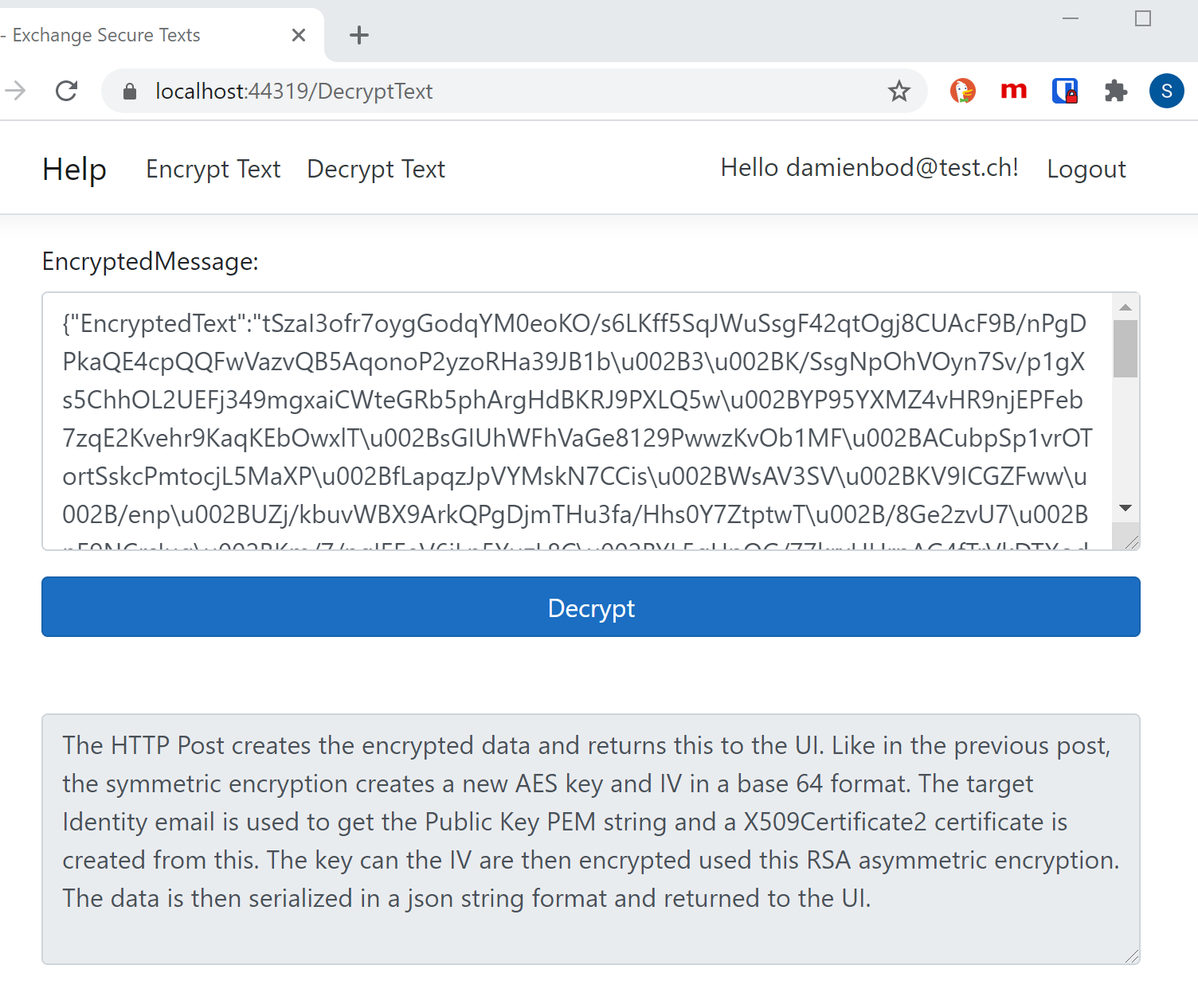
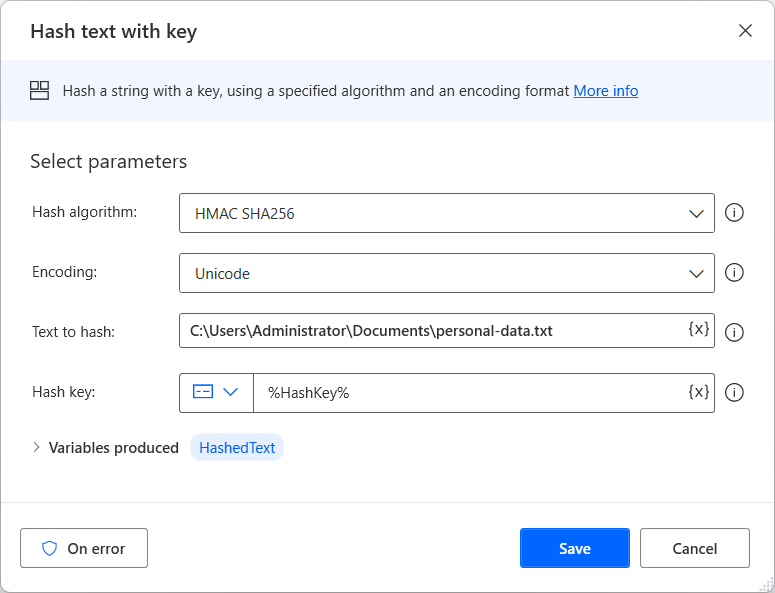
Encrypting texts for an Identity in ASP.NET Core Razor Pages using AES and RSA | Software Engineering
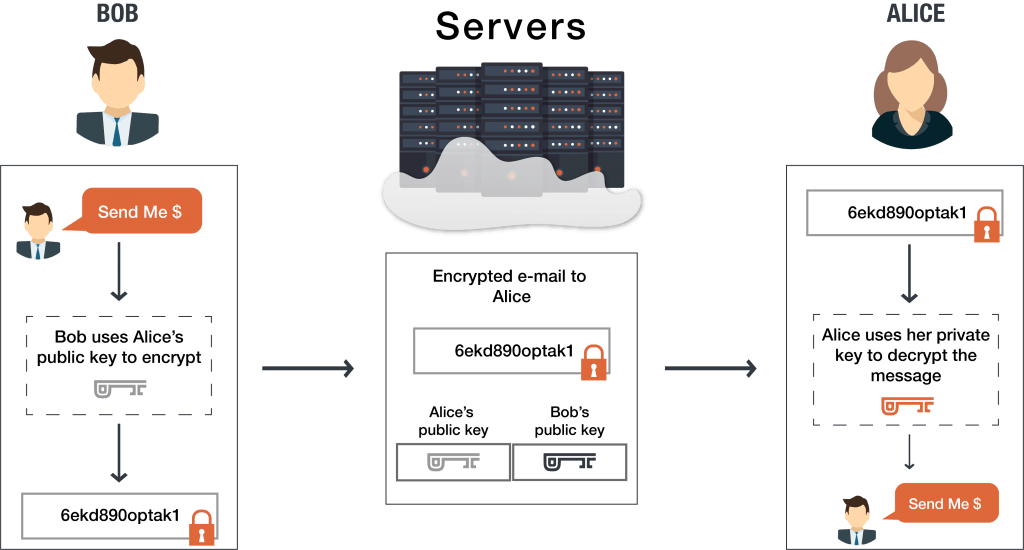
A Deep Dive on End-to-End Encryption: How Do Public Key Encryption Systems Work? | Surveillance Self-Defense
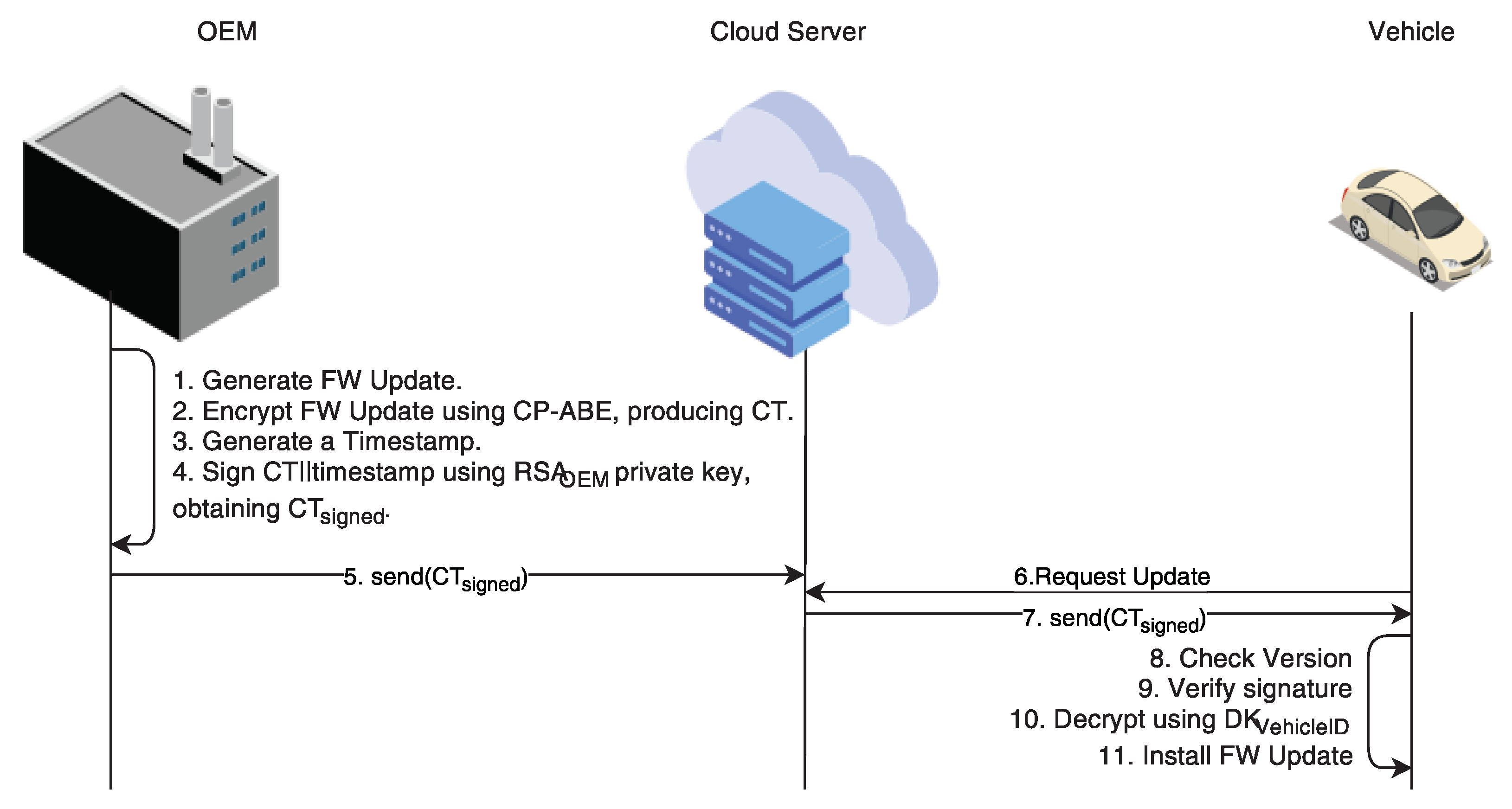
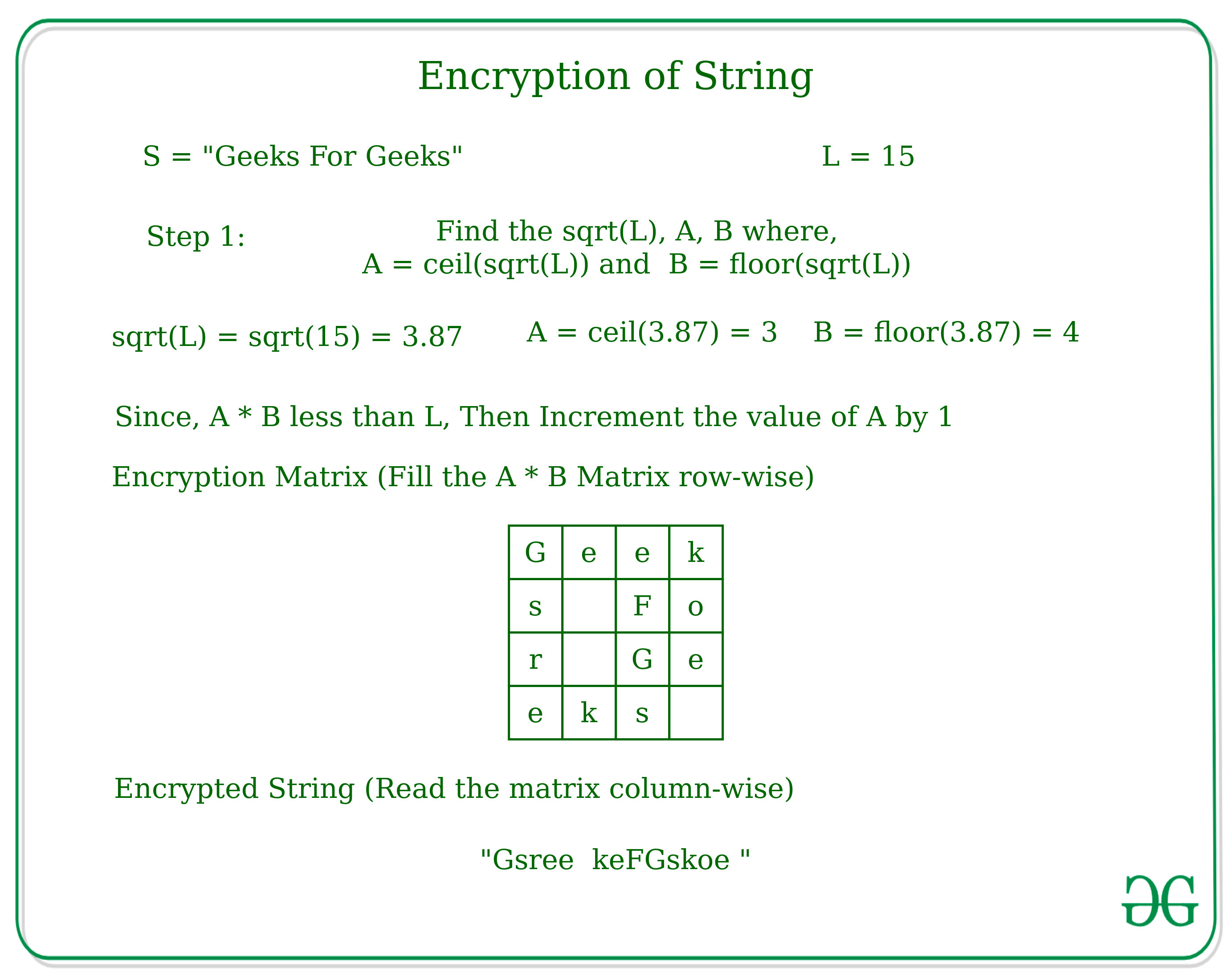
Sensors | Free Full-Text | Performance Evaluation of Attribute-Based Encryption in Automotive Embedded Platform for Secure Software Over-The-Air Update
![Binaryworld - Encrypt/Decrypt file using Microsoft Crypto APIs (With User specific c ... [ VB -> Cryptography ] Binaryworld - Encrypt/Decrypt file using Microsoft Crypto APIs (With User specific c ... [ VB -> Cryptography ]](https://binaryworld.net/Main/Articles/Lang1/Cat18/Code3766/screen3766.jpg)
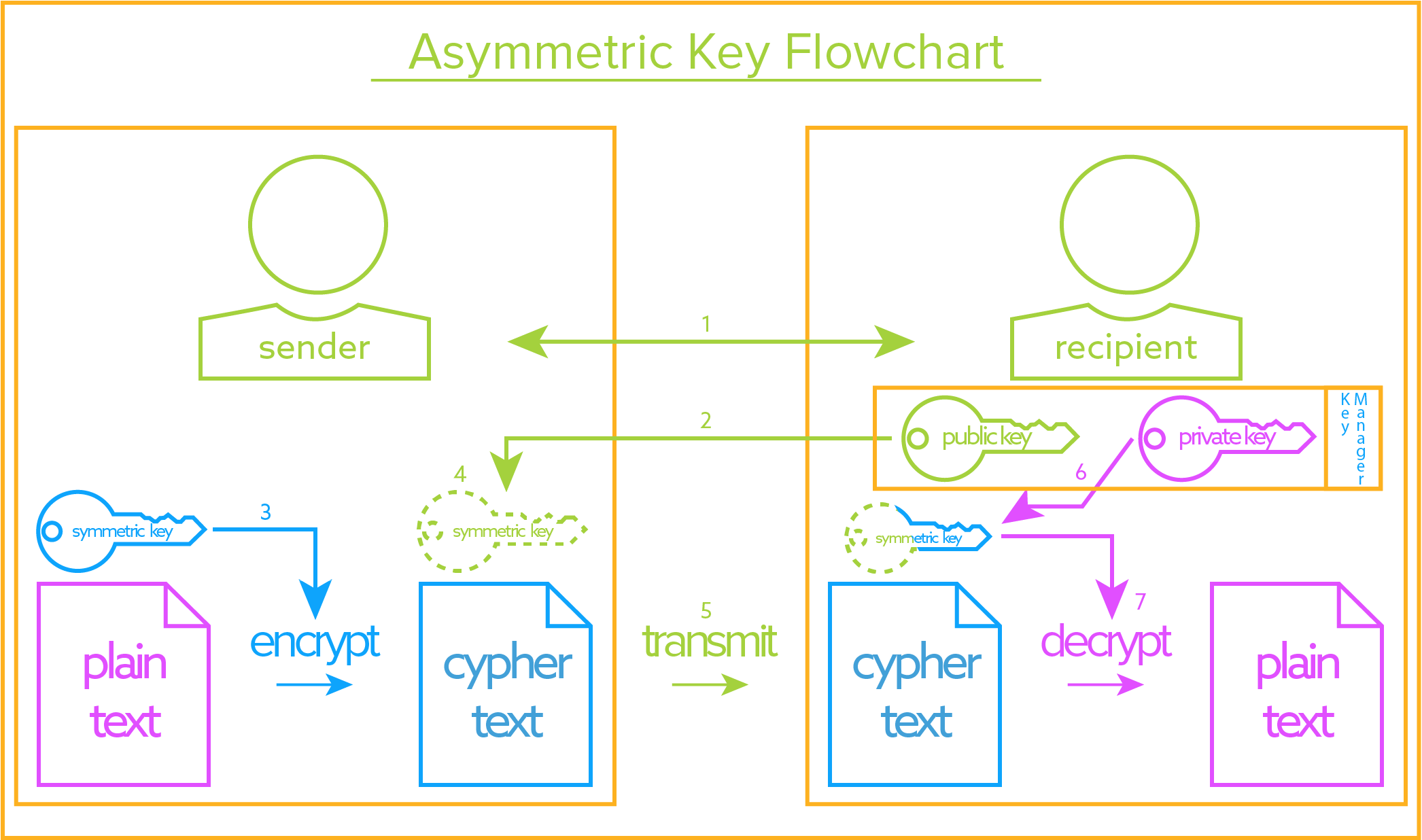

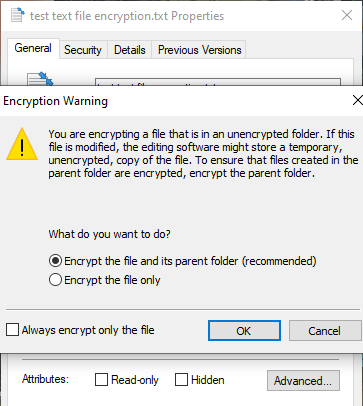



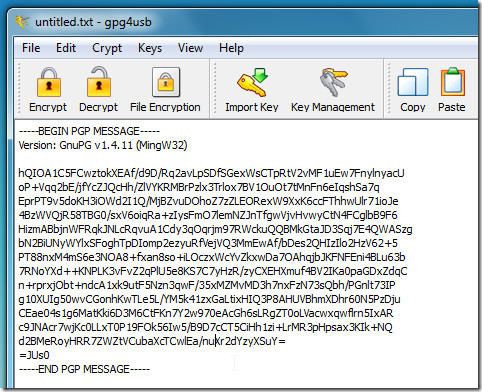

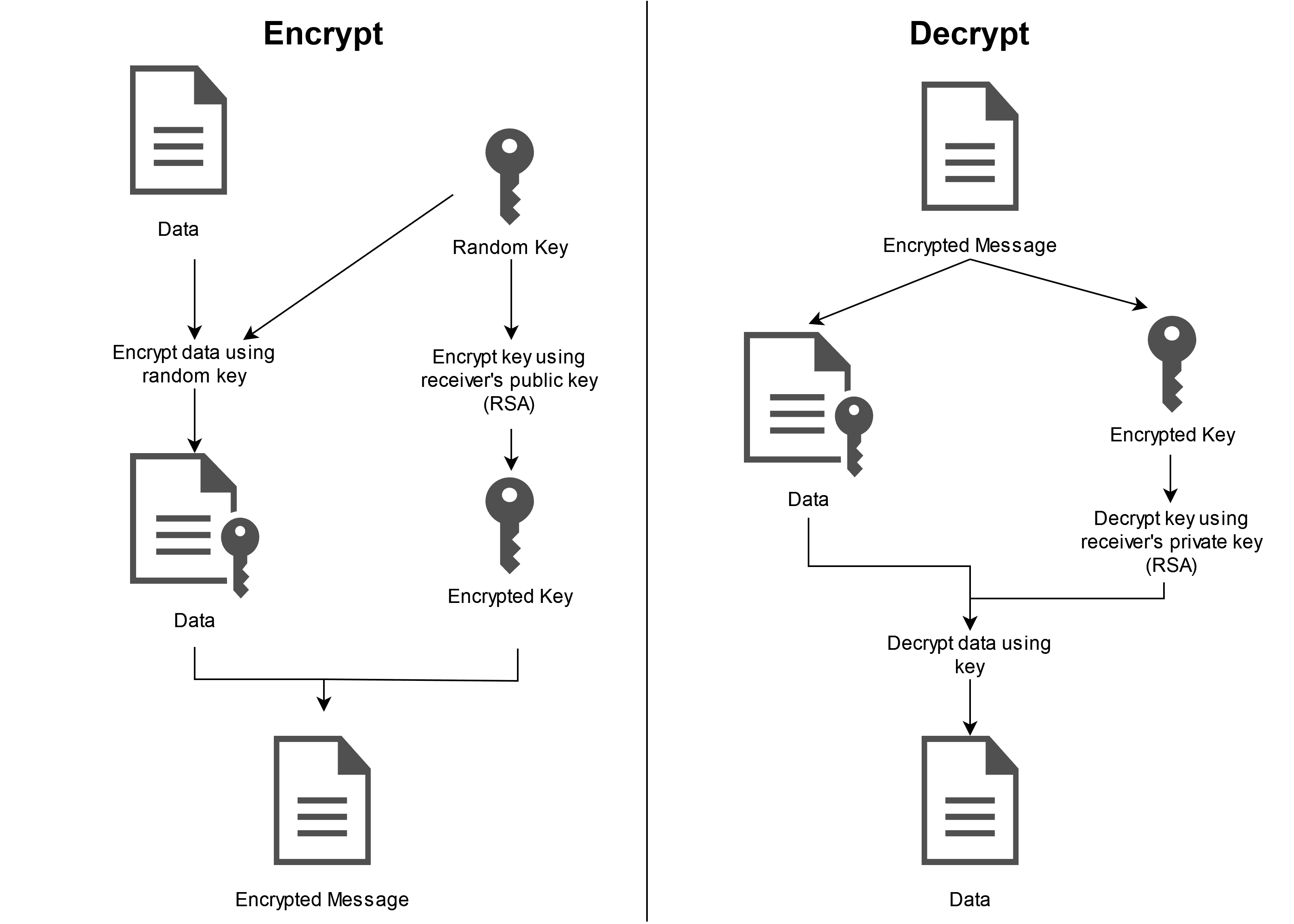


![Encrypt / Decrypt Sensitive Data in Excel Spreadsheets Using CellShield [video] - IRI Encrypt / Decrypt Sensitive Data in Excel Spreadsheets Using CellShield [video] - IRI](http://www.iri.com/blog/wp-content/uploads/2014/08/DataEncryptAlpha.png)