![PDF] Proactive vs. Reactive Security Investments in the Healthcare Sector Proactive vs. Reactive Security Investments in the Healthcare Sector | Semantic Scholar PDF] Proactive vs. Reactive Security Investments in the Healthcare Sector Proactive vs. Reactive Security Investments in the Healthcare Sector | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1fcf353f878db23be00edc443625bf3ef3d94b73/34-Figure1-1.png)
PDF] Proactive vs. Reactive Security Investments in the Healthcare Sector Proactive vs. Reactive Security Investments in the Healthcare Sector | Semantic Scholar

Imbalance between proactive and reactive cybersecurity | ThreatWorx Cyber Attack Prevention Platform

Proactive vs. Reactive: How Savvy Use of Analytics Helps Contact Centers Navigate and Adapt to Uncertainty | NICE

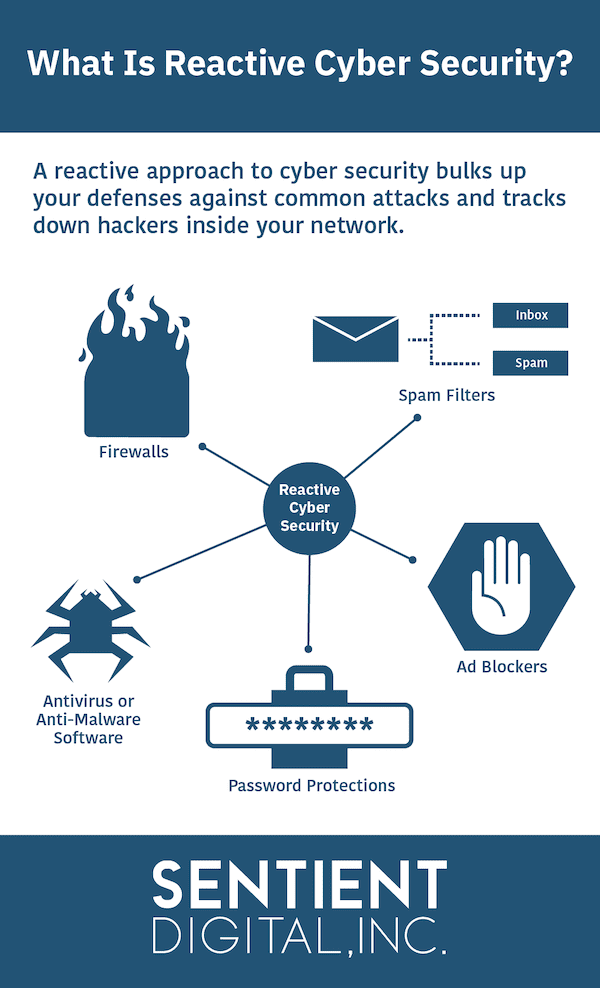
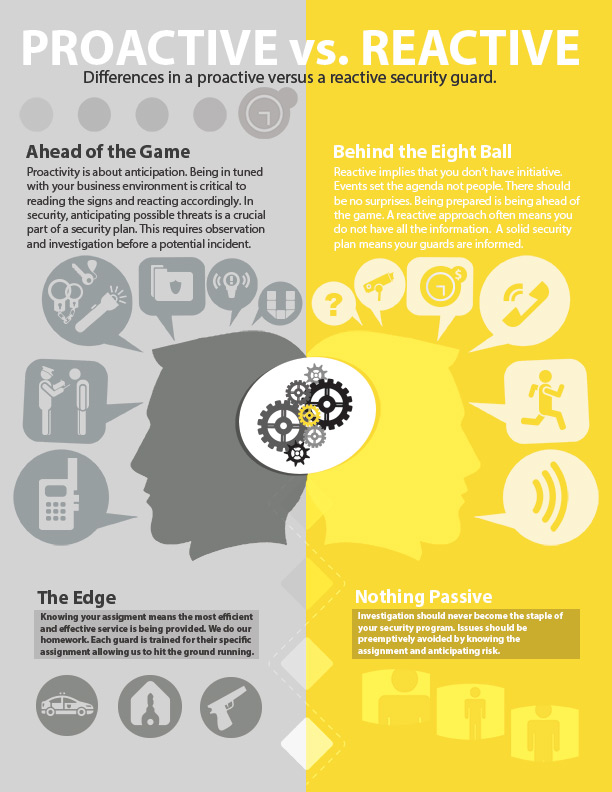
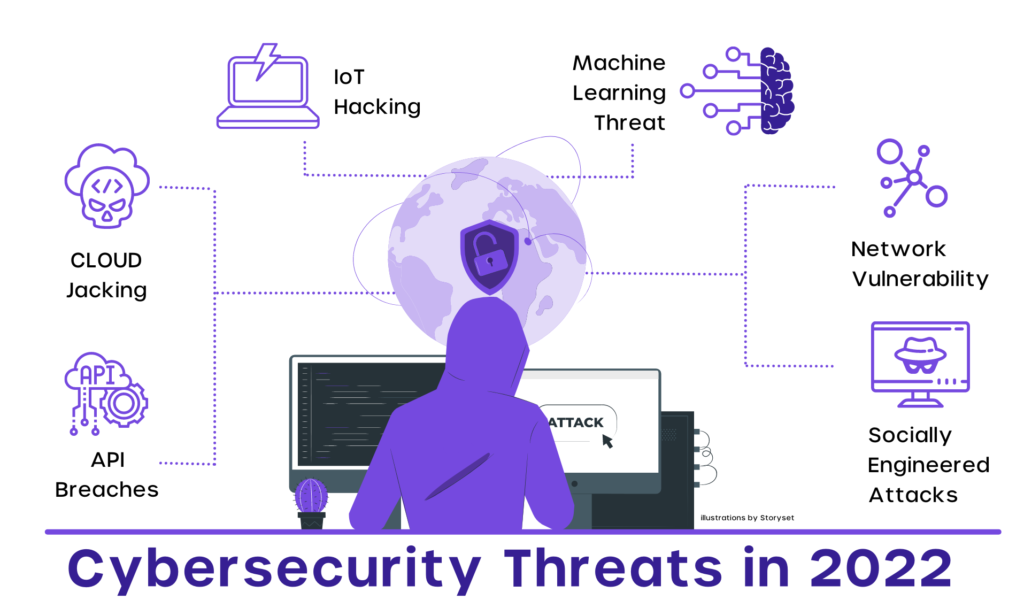
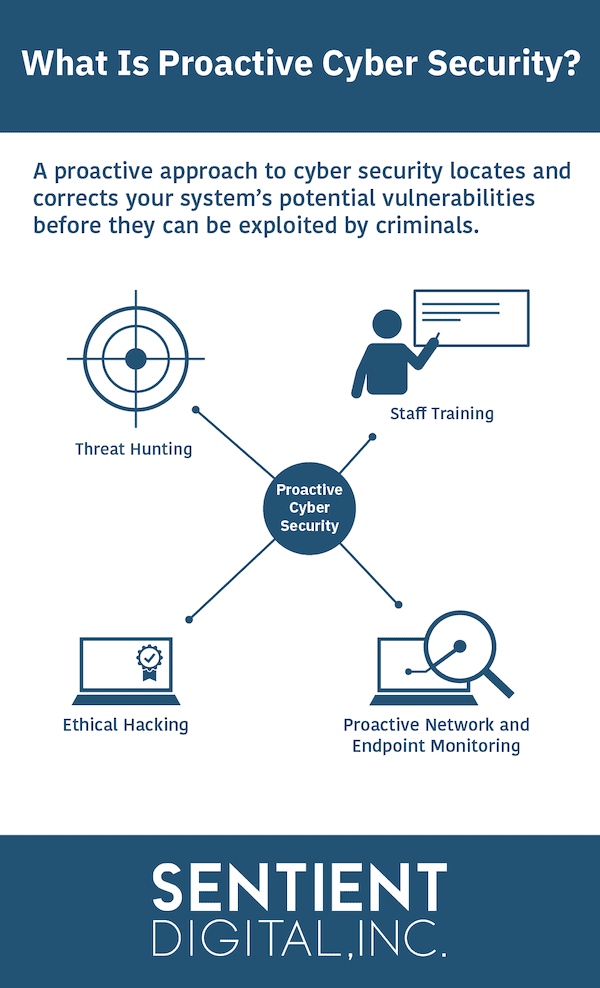
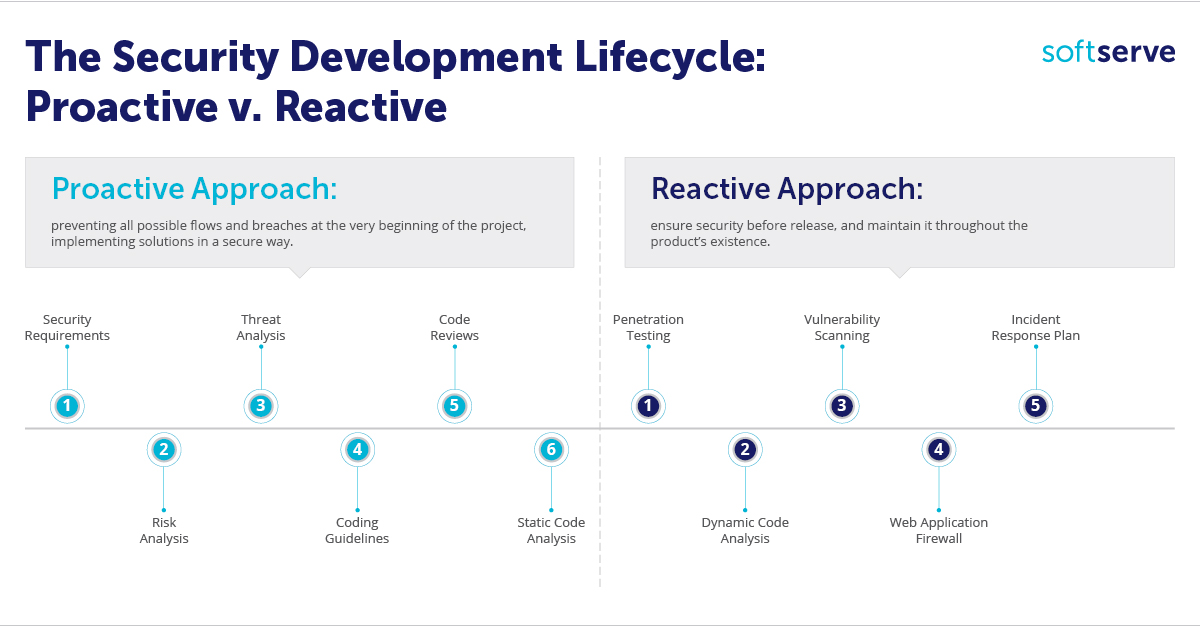
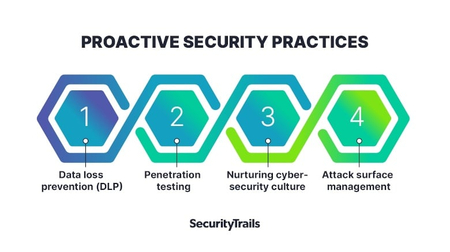
Cybersecurity Prism - ✴✴What is proactive vs reactive cyber security?✴✴ Proactive cyber security involves identifying and addressing security risks before an attack occurs, whereas reactive cyber security involves defending against attacks that