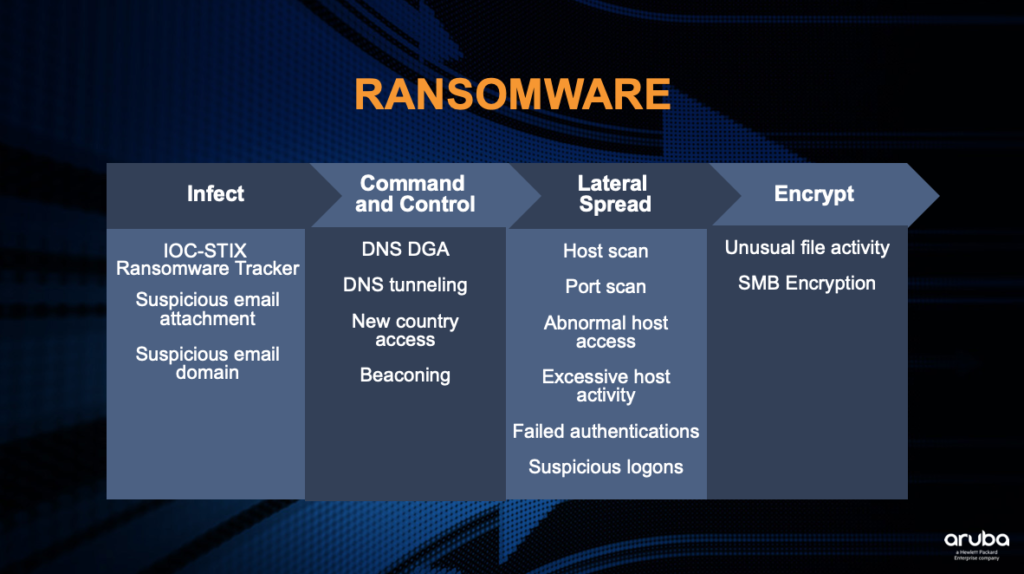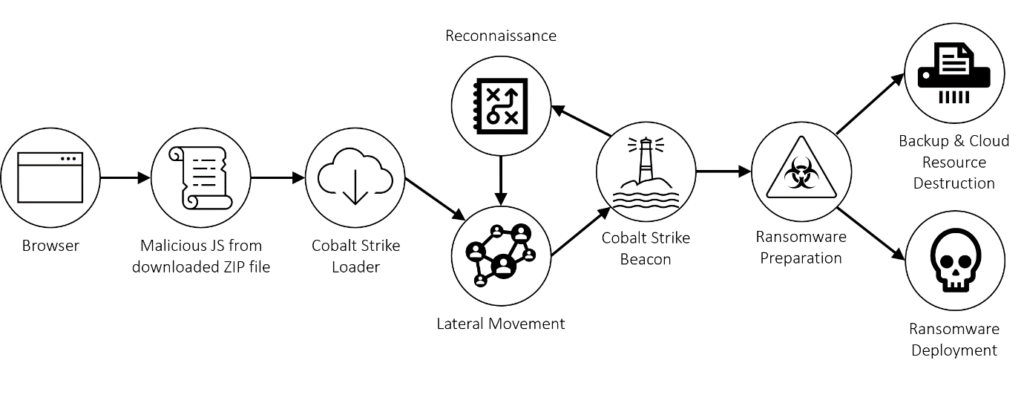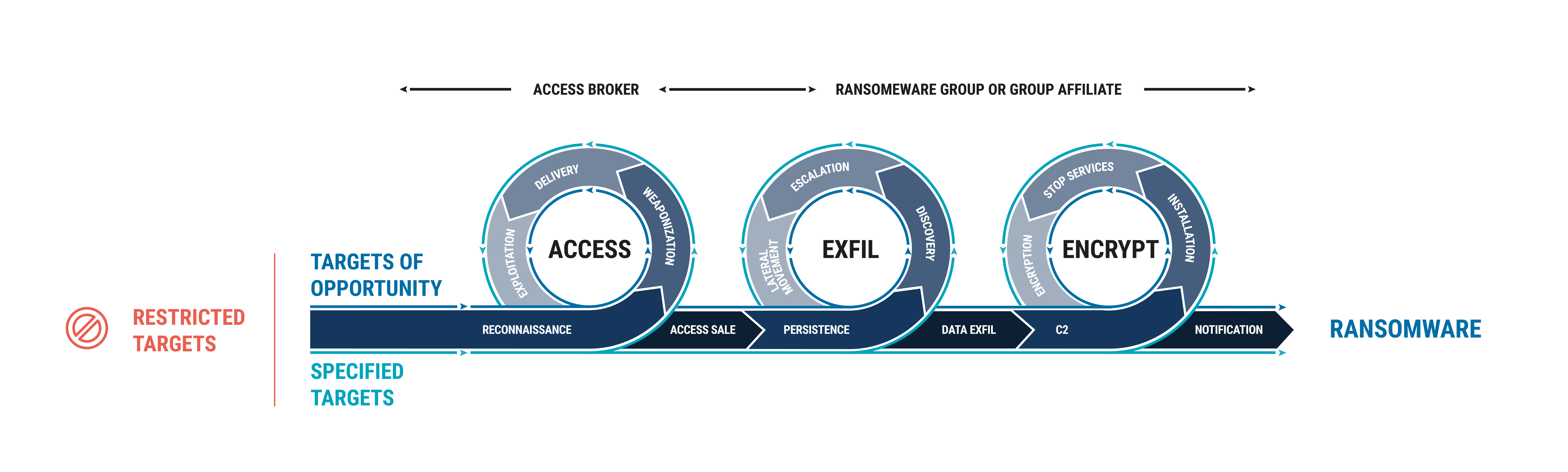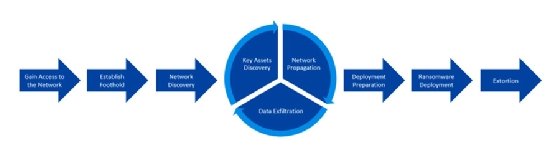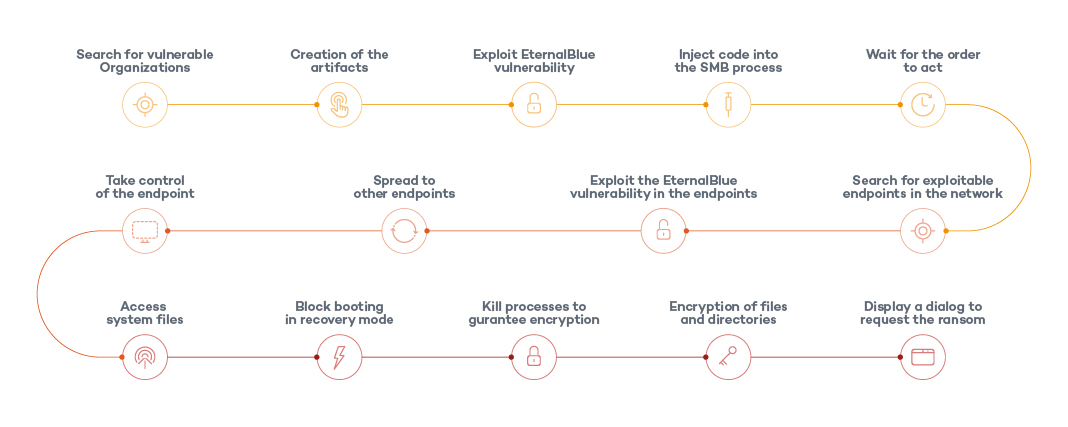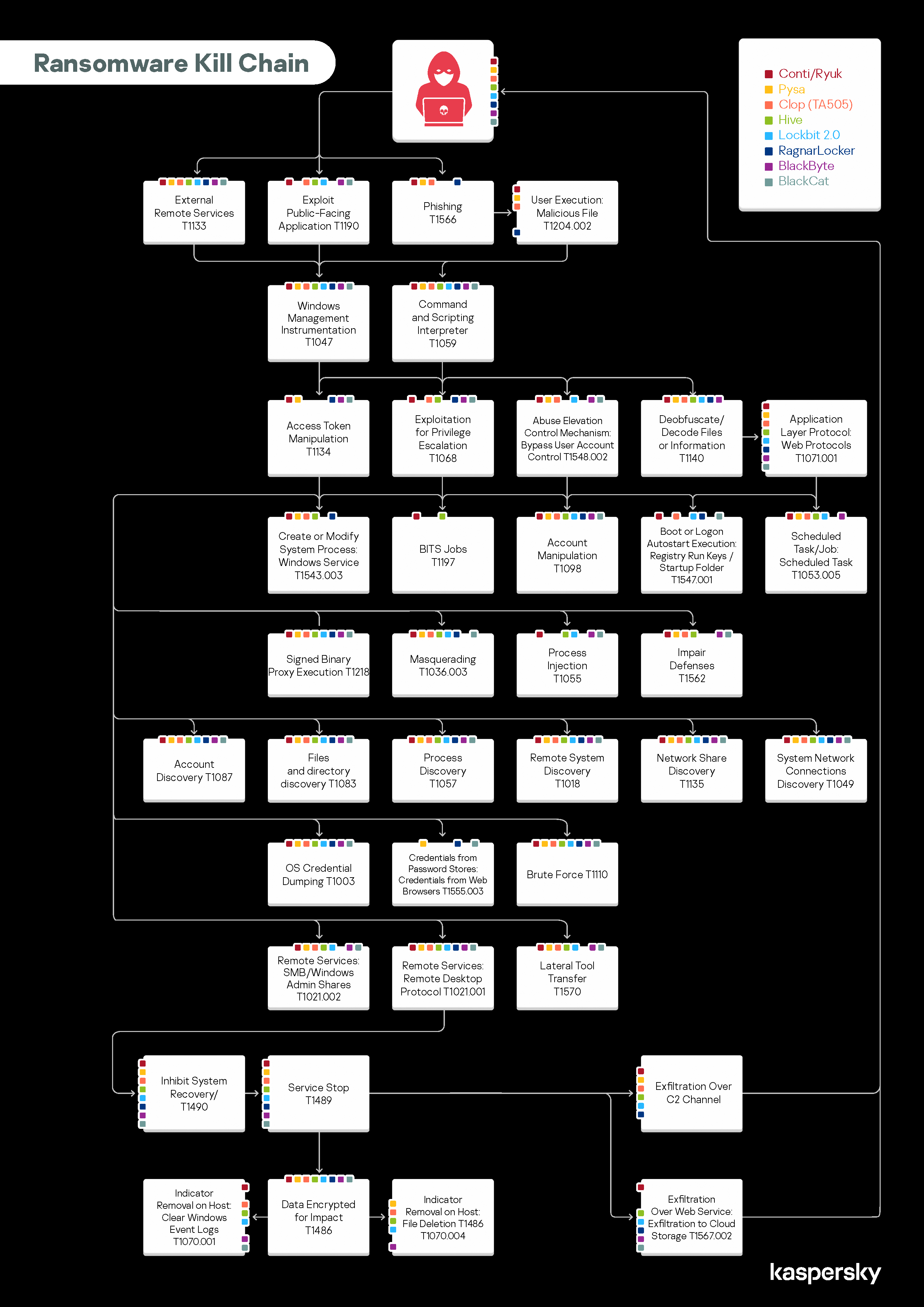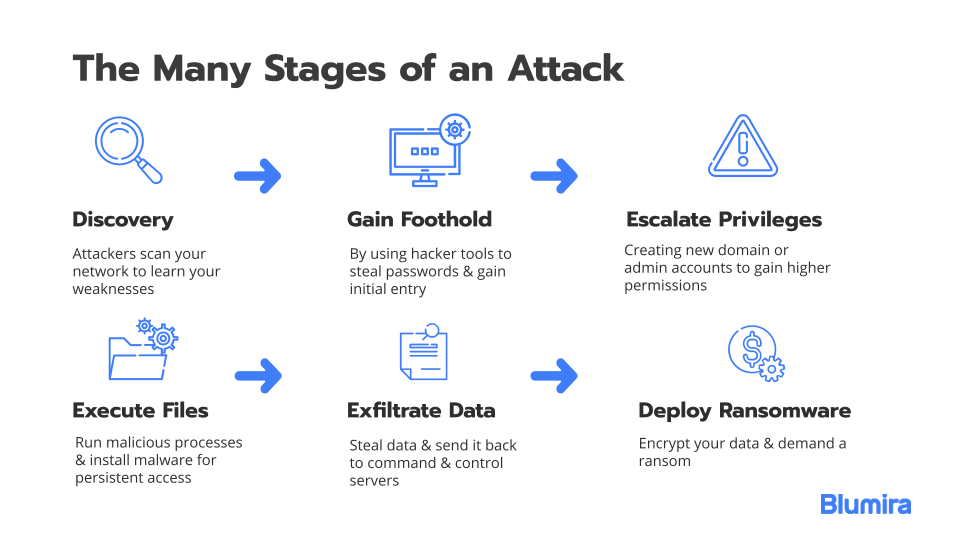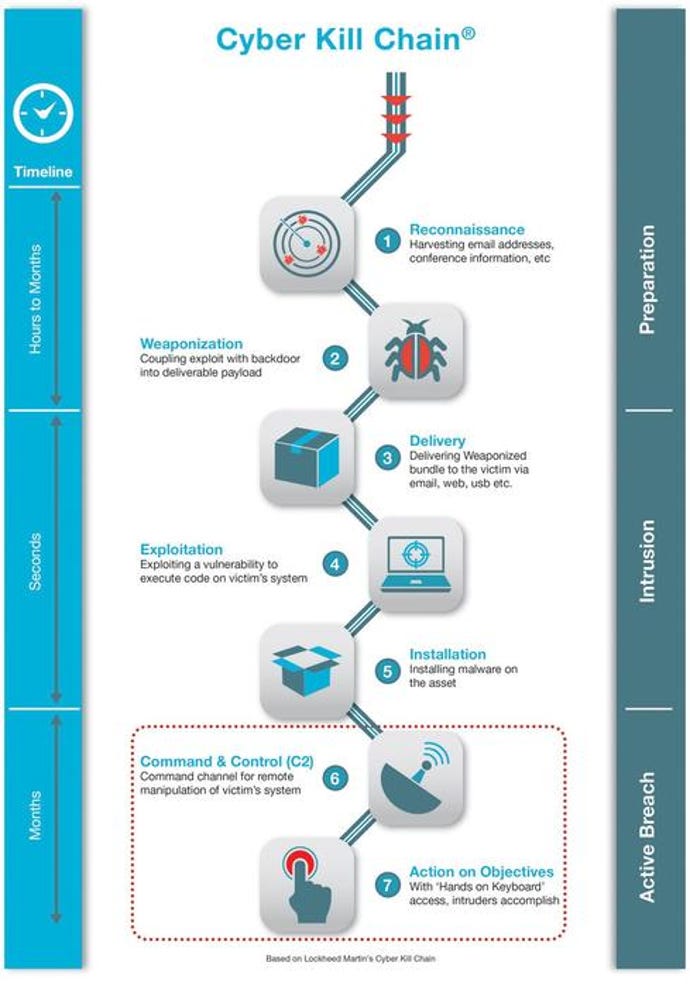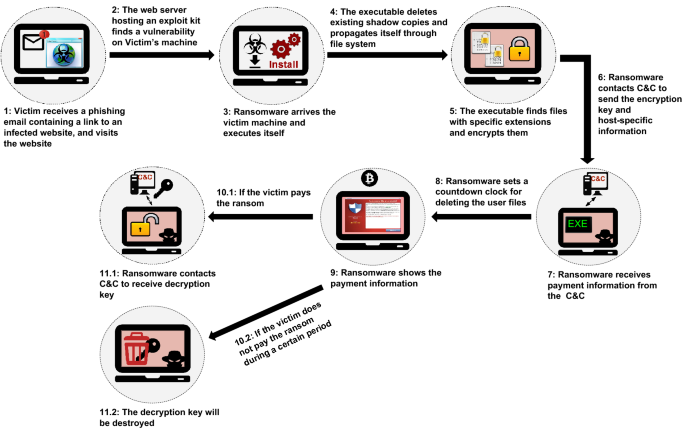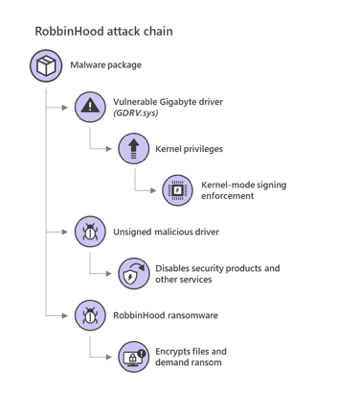
Ransomware Characteristics and Attack Chains – What you Need to Know about Recent Campaigns | Tripwire

NoGoFallMaga on Twitter: "3/ Our speaker then drew our attention to the ransomware kill chain which is how bad actors make use of ransomware He then talked about the 3 stages of

Cyber Startup Observatory on Twitter: "The Ransomware Kill Chain Available for download in Press Quality: https://t.co/2ctw6MLUnq For further information on cyber topics & innovation: https://t.co/PRz5R1HD6M #CyberSecurity #InfoSec ...

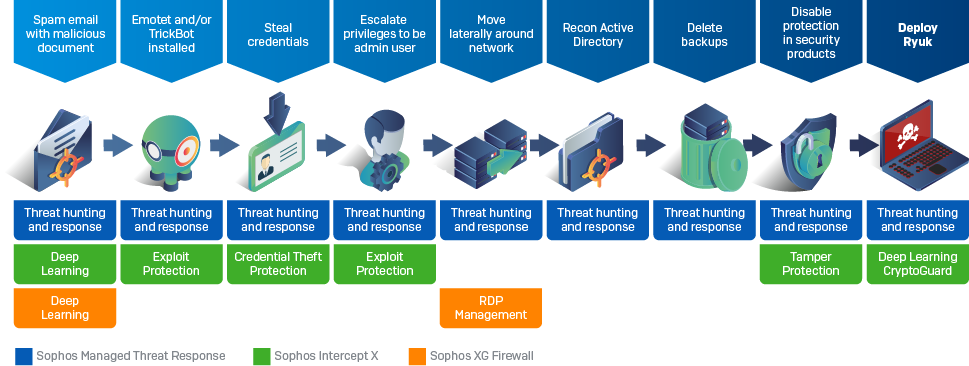
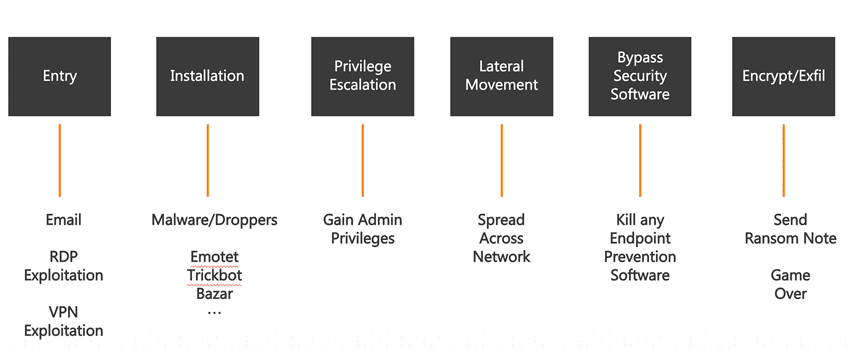
![What is Maze Ransomware? [Technical Analysis] | CrowdStrike What is Maze Ransomware? [Technical Analysis] | CrowdStrike](https://www.crowdstrike.com/wp-content/uploads/2020/12/Preempt-Maze-blog-image.png)