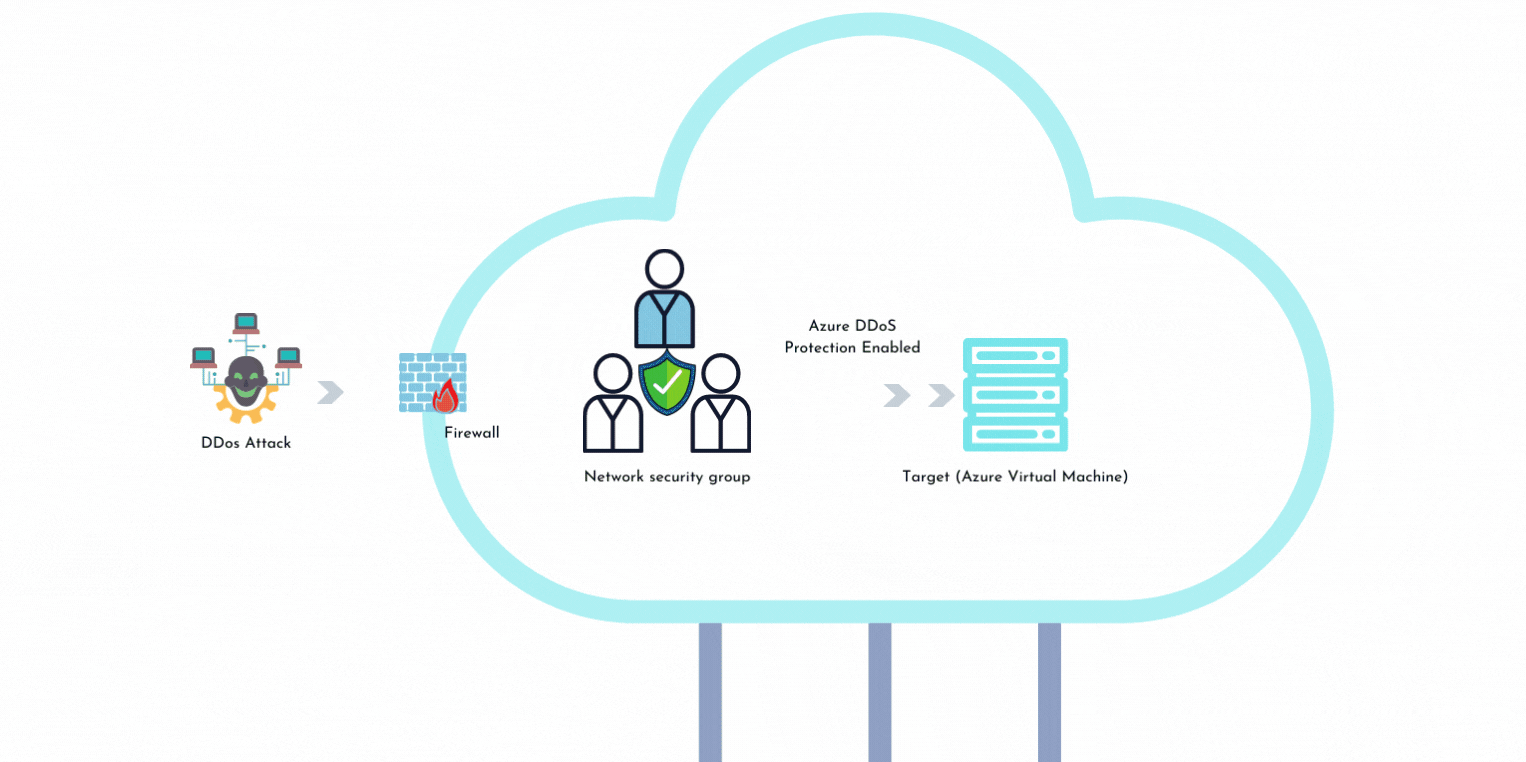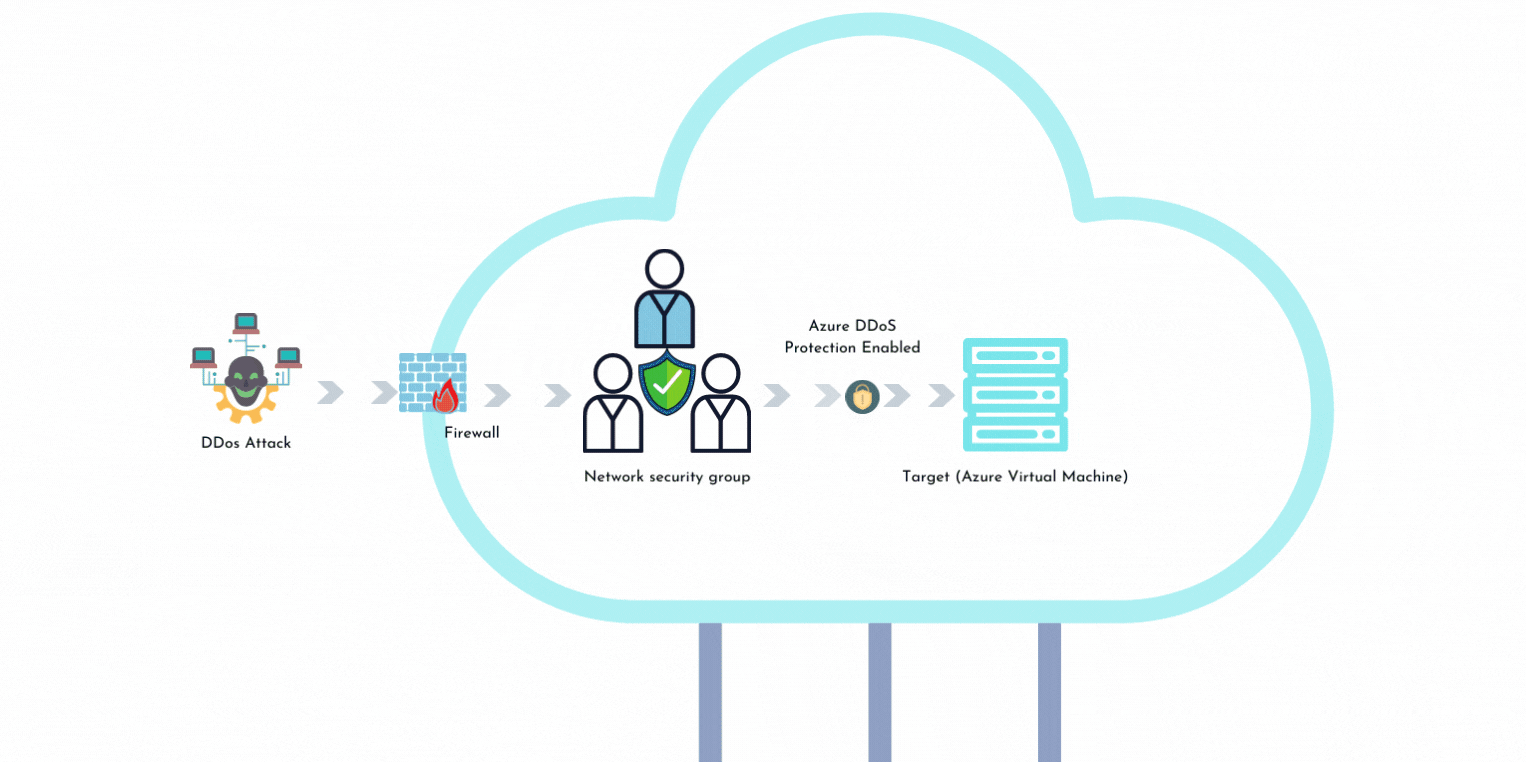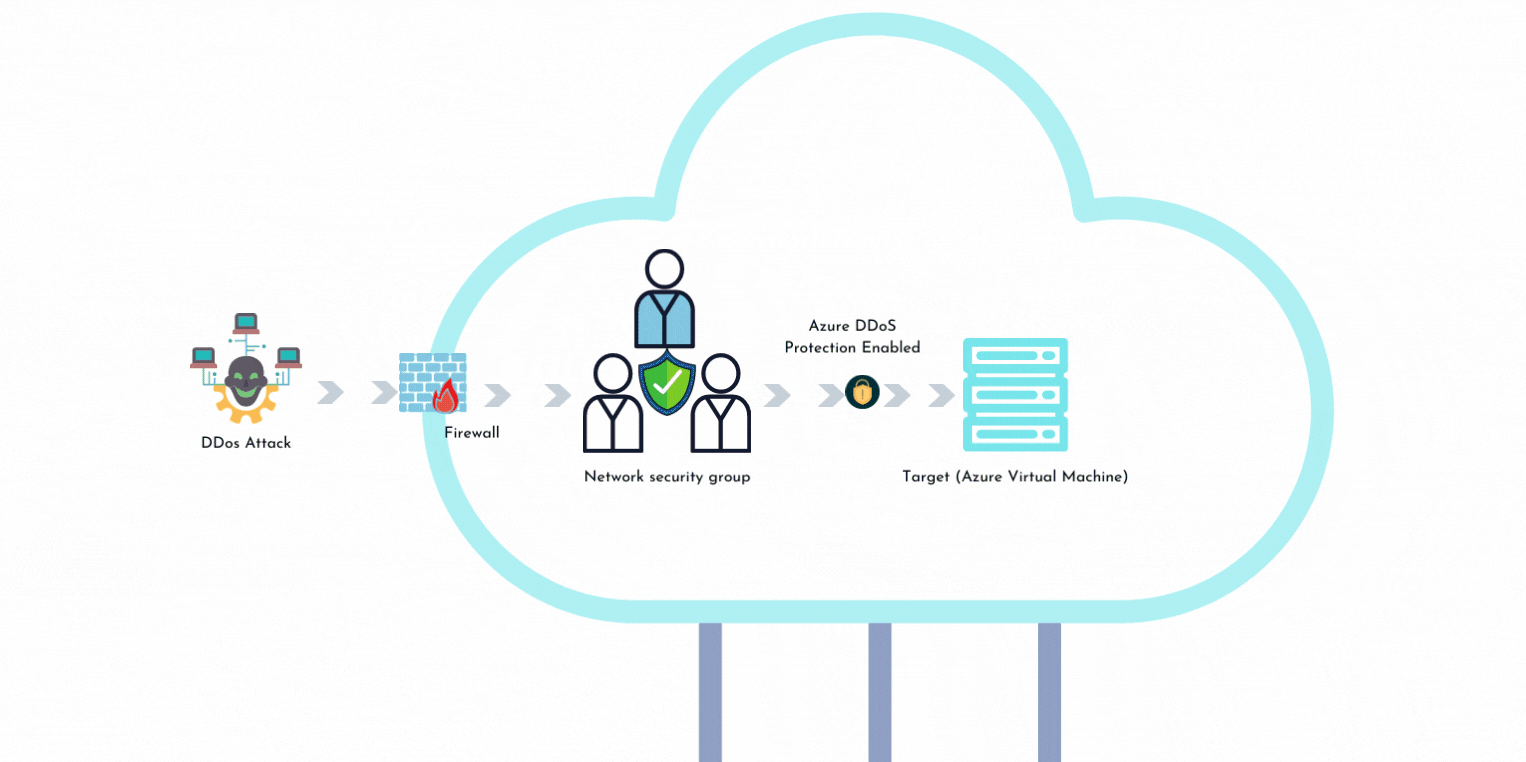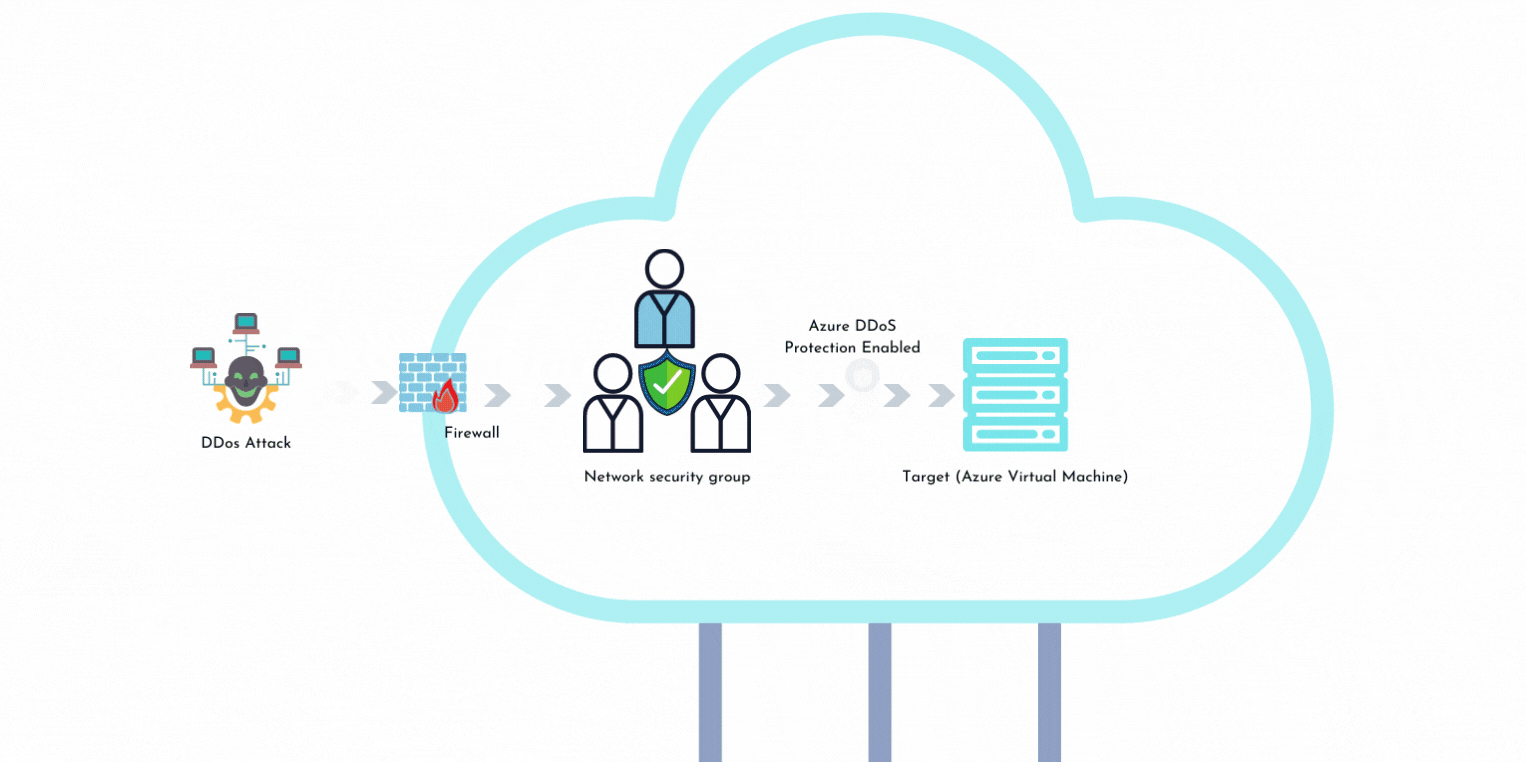
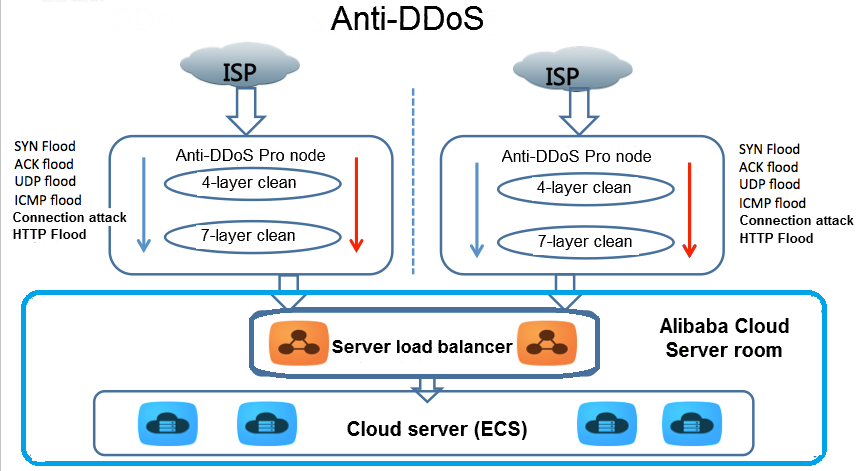
2017 DDoS and Web Application Attack Landscape - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.
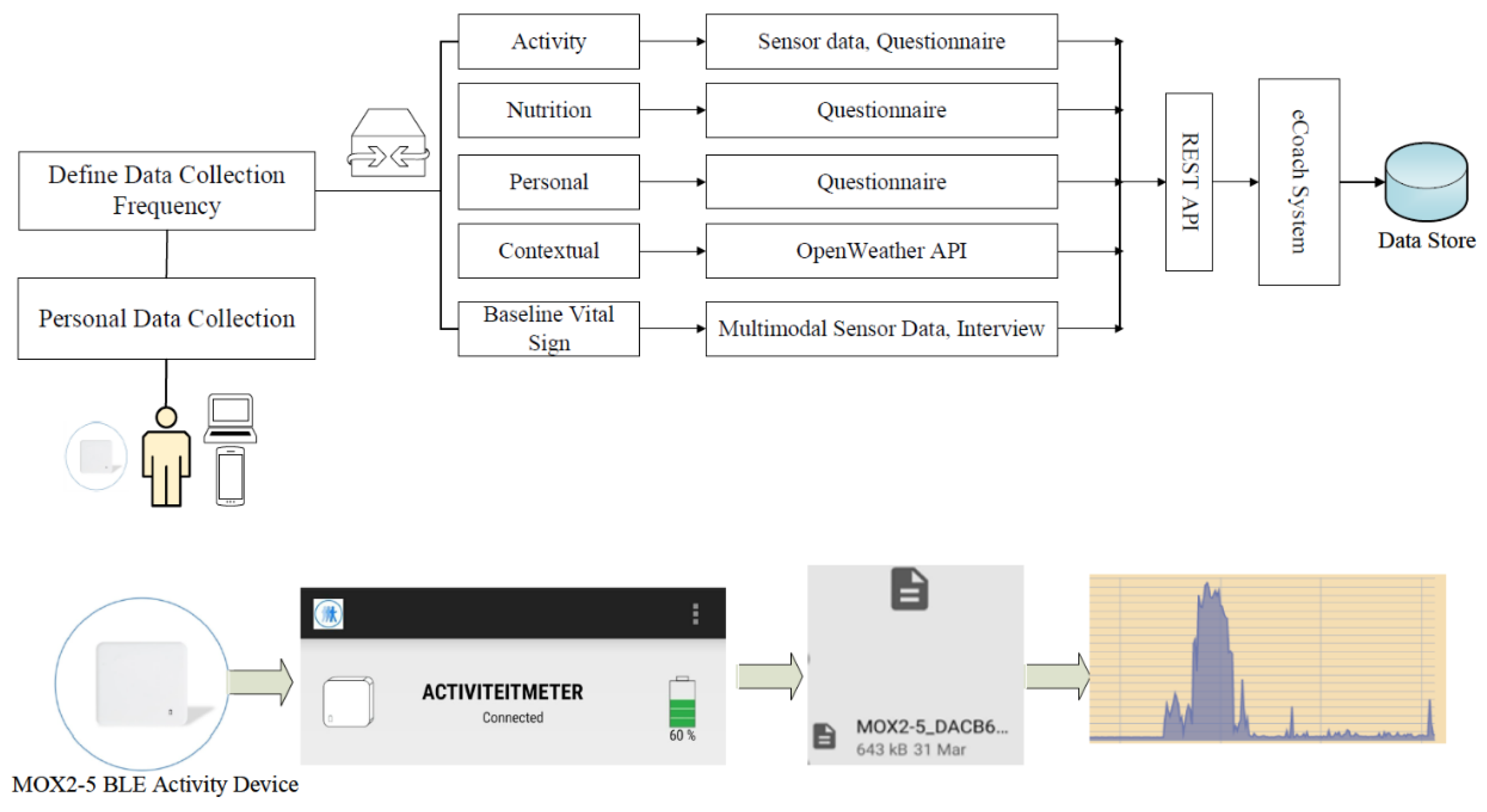
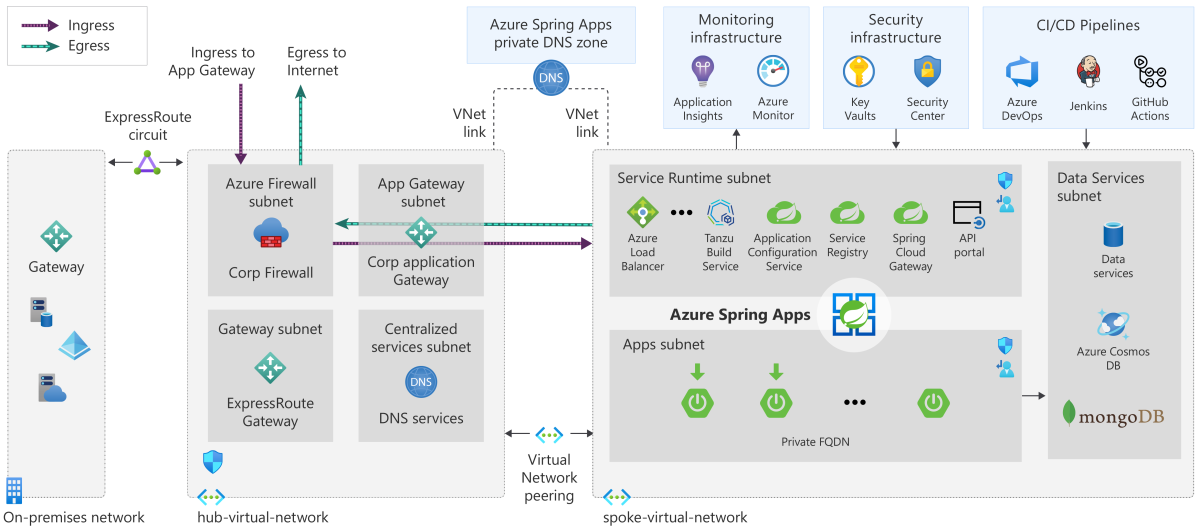
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study

Java Tips and Tricks: Protecting Spring Boot Restful API from DDoS Attack with Bucket4j in 5 minutes - YouTube

Java Tips and Tricks: Protecting Spring Boot Restful API from DDoS Attack with Bucket4j in 5 minutes - YouTube
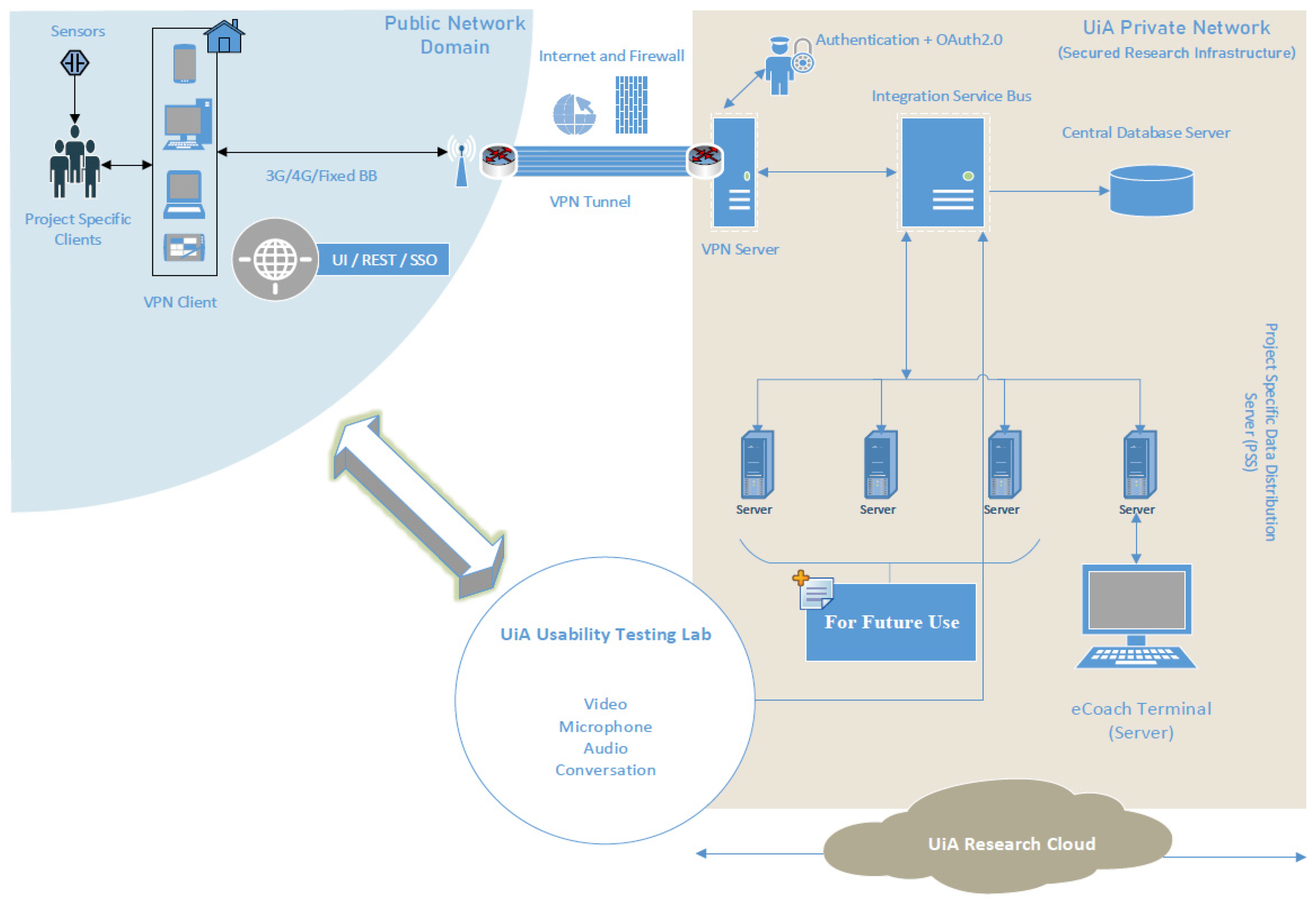
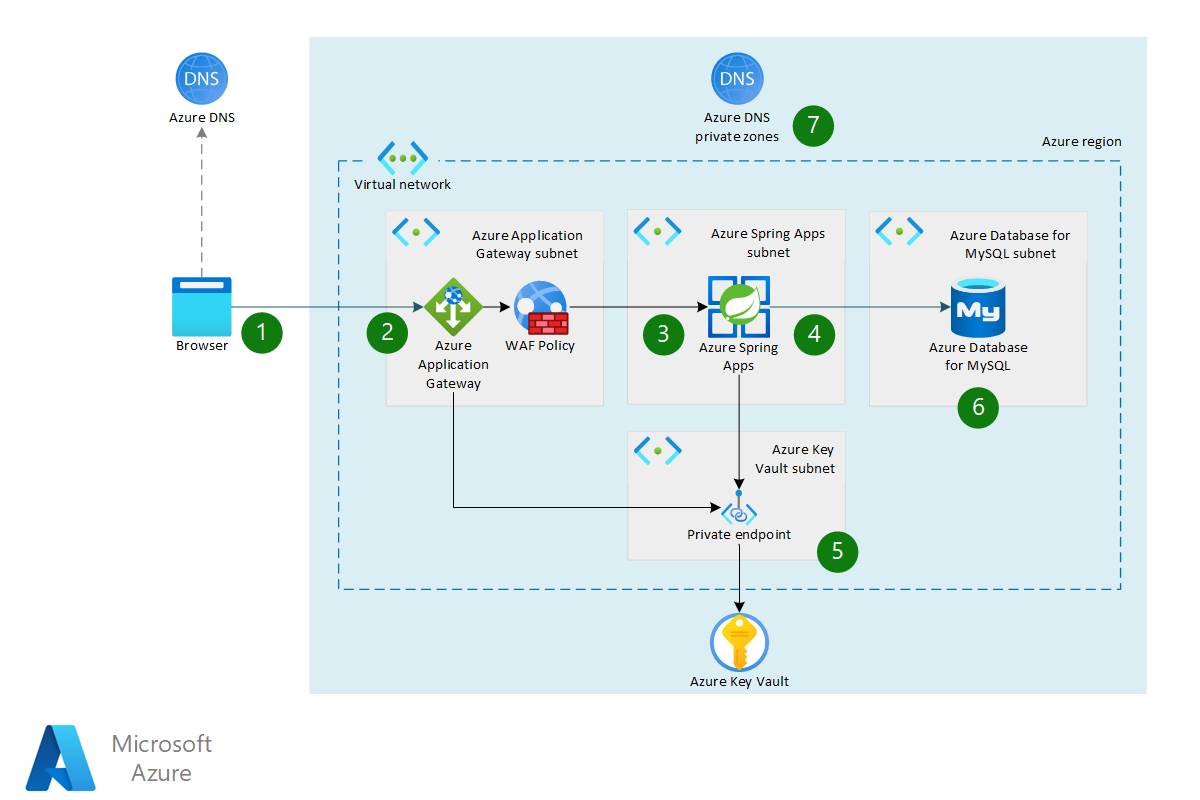
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study
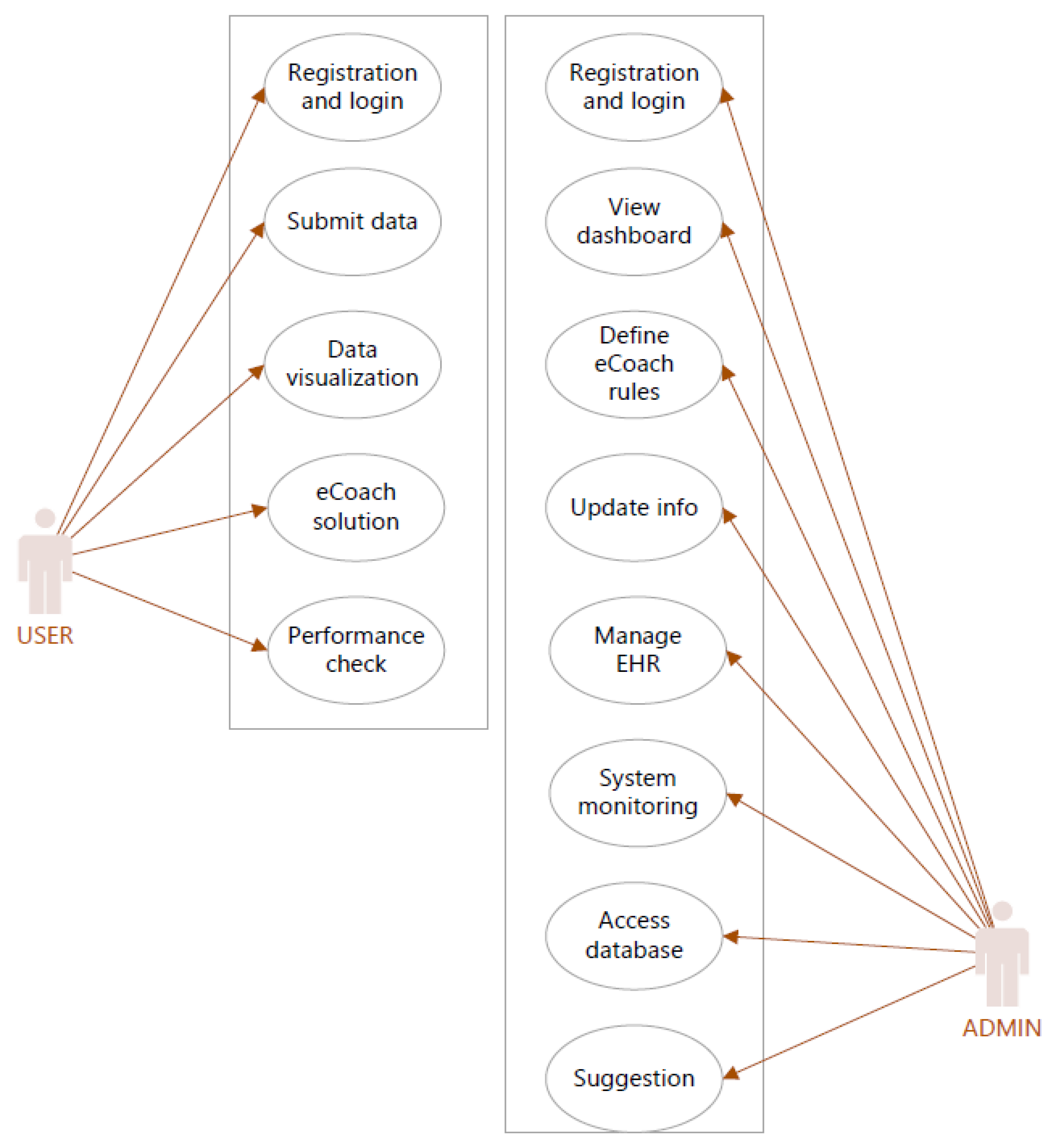
Sensors | Free Full-Text | Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study
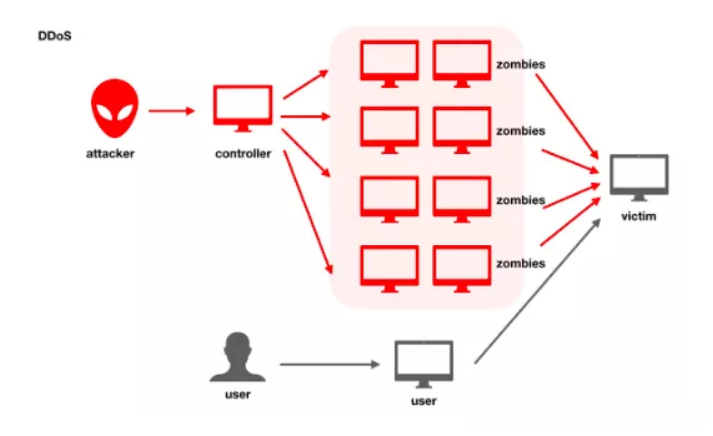
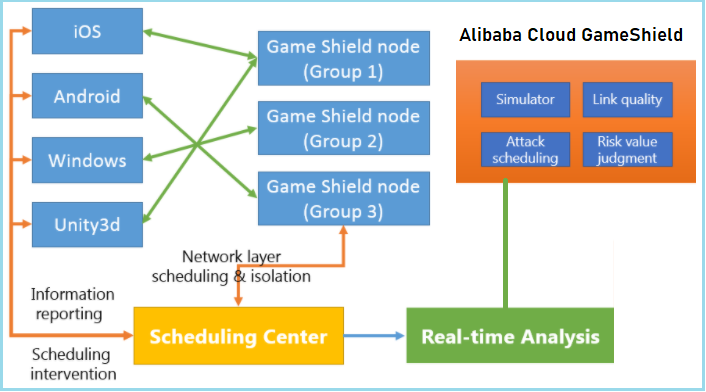
Defending against TB-level Traffic Attacks with Advanced Anti-DDoS systems - Alibaba Cloud Community

Observations from a Log4j Decoy: From Vulnerability to Infection to DDOS in Record Time - Fidelis Cybersecurity